How can we help you?
Is BSRS Secure?
SECURITY MODEL
The BSRS security model defines the essential aspects of security and their relationship with each operating layer. It provides the required level of understanding on what the implemented key protection are features via the simplified OSI layer.
The security model also helps to ensure that Confidentiality, Integrity, Availability are effectively applied throughout the system.
BSRS - security implementation is based on the started security practice in the industry. All the security features that have been included are in accordance with existing Philippines Cybersecurity and Data Privacy Act.
INFRASTRUCTURE VULNERABILITY ASSESSMENT
Vulnerability Assessment is a process of identifying the vulnerabilities of an application and network infrastructure. Also, Vulnerability Assessment enables us to be aware of all risks and weaknesses inside our Infrastructure that poses a threat that could lead to security breaches such as exploit attacks or social engineering.
To ensure that our system is foolproof to any kind of security risks, we will perform a VA scan using the VA Scanner tool to our application and all Infrastructure involved in this project.
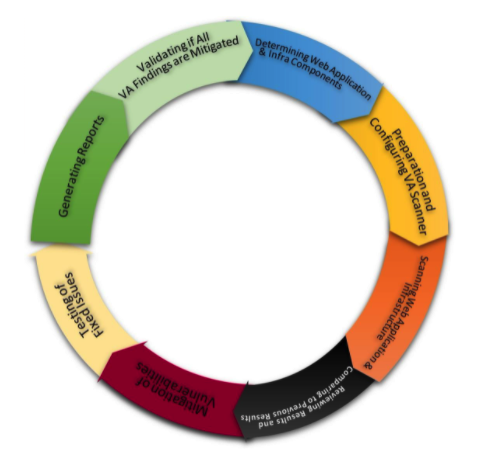
WEB APPLICATION VA SCANNING FLOW
|
|
All VA findings of EMS Application will be mitigated and will go through a series of VA scanning processes until the closure of all the open findings. VA scan will be executed on a quarterly basis for both application and server levels to ensure all security risks have been covered. The vulnerability database available with the US NIST (National Institute of Standards Technology) and US CERT (Computer Emergency Response Team) will be used as reference.
Following are the layers for Vulnerability Assessment:
Application Layer
Web Layer (external and without WAF) Server Layer and Ports
BSRS inherits the security policies and guidelines of TESDA. BSRS Security incident plan and response mechanism is also enforced.